Lately I’ve had a number of customers and clients calling me about either a “person who called them from Microsoft saying their system is infected” or a “voice on their computer telling them to call a phone number to fix their system”. These type of computer security scams are becoming more and more prevalent and are tricking a large number of innocent computer users into shelling out large sums of money to “fix” a problem they don’t actually have. Or worse, leave them stranded with an inoperable system.
This is essentially a new-age version of a snake oil scam. While the methods that are used to execute these scams vary, their end goal is the same: to extract money and credit card information from the ill-informed. Fortunately, these scammers are easy to stop with a little bit of know-how. In this article, I’ll cover both the phone and website versions of these scams, and how you can remove the problem and avoid being swindled.

The Man from “Microsoft”
The first thing we’ll look at is actually one of the oldest scams in the book: the cold-calling imposter.
Here’s the situation: You receive a phone call from a person claiming to be from Microsoft, your computer security provider (Norton, McAfee, etc), or your Internet provider. This person tells you that their system has detected malicious software on your computer, a faulty system component or, in some cases, illegal activity. They request that you go to your computer and allow them to take care of the problem for you. If you don’t do this, you will be charged with a crime, have all your personal information stolen, or will be locked out of all of your banking, email, and social media accounts. This “important” procedure will only cost you a nominal fee of $400 and will “guarantee” your system is free from problems.
While it may sound very legitimate and scary, this is nothing more than a scam to swindle you out of your $400. The best way to avoid having this happen to you is to remember a rule that will help you easily sniff out this scam:
“Microsoft Will Never Call You”
Unless you initiate contact with them, you will never receive a phone call from Microsoft, your computer manufacturer, an anti-virus company, or likely even your Internet provider. Let alone one that tells you there is something wrong with your computer. These companies communicate with their customers as well as the general public through public announcements, not personal phone calls or emails. The rule to live by here is: if you weren’t expecting the phone call, it’s likely not legitimate.
Of course, you may personally receive communications from some of your software or service providers that is legitimate. Your Internet provider may issue you an automated phone call saying they’ll be performing service to the lines in your area. Or, if there has been illegal activity on your Internet connection, they may issue a sternly worded letter or email. If you’ve opted into it, you may receive newsletters or other email communications from your Anti-Virus company. You will not, however, ever receive a call from them stating your computer is infected or otherwise broken.
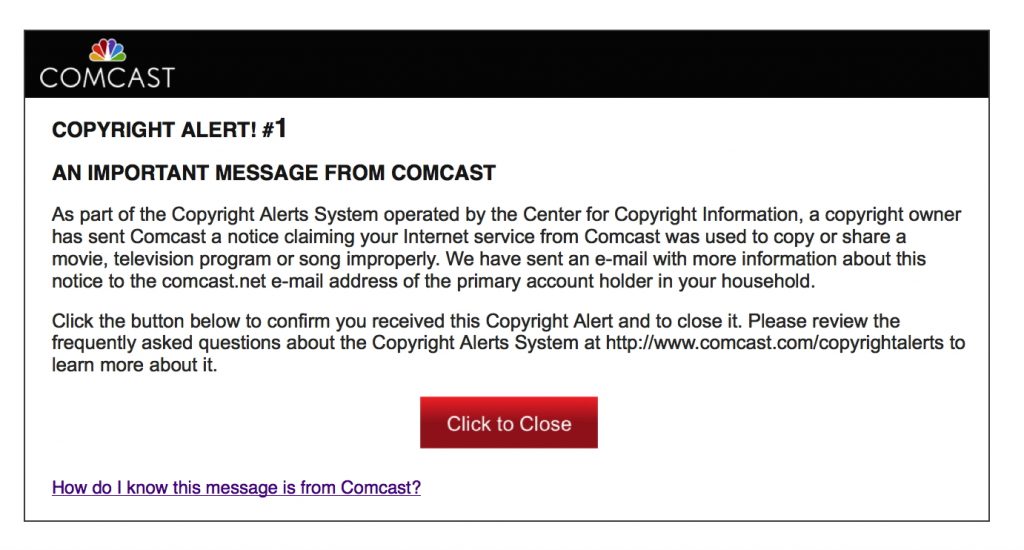
If your ISP does contact you, it will be through email, written letters, or messages like the one above.
Another good thing to remember is that you will never be asked by any company to allow a person to remote into your computer unless you have requested assistance from that company for a problem you are having. It is vitally important to remember that, if you do find yourself on the phone with a scammer, you do not allow them remote access to your computer! As soon as you allow them access, it’s game over as they can effectively do whatever they want.
So how do you deal with the situation I listed above? The same way you would deal with any other phone scam or telemarketer. You can simply hang up the phone. Or you could try and gather as much information as possible about them and their company as possible and file a complaint with the FCC. Going forward, you can help keep yourself from getting any of these calls in the first place by putting your number on the National Do Not Call Registry. While this won’t guarantee you’ll never receive a call, the penalties are harsher for the offenders and it makes reporting them somewhat easier as well.
So now that we’ve taken care of the phone side of things. Lets take a look at the other version of this increasingly popular scam:

My Computer’s Talking To Me!
So this time, you’re on your computer browsing your favorite website or perhaps looking up some information when suddenly a flashy warning page appears on your screen and a voice starts coming through your computer speakers warning you that your system is compromised and that you need to call the telephone number on your screen for immediate assistance. Your computer is seemingly locked down, you’re unable to close or navigate away from the page and you have no idea what to do next.
This version of the scam is called a Browser Hijack (Tab Hijack is another name for it). While it differs from a phone scam in how it’s executed (as well as how you deal with it) the end result is the same: it’s nothing more than an attempt to swindle you out of a sizable amount of money.
Like the phone scam, Browser Hijacks can come in many different varieties. Some will be obnoxious with background voices/noises and flashing pages that should have a seizure warning on them. Others will be more subtle and official looking trying to pose as a communication from a security or software company. The one constant is that they all will want you to immediately connect with a “remote support agent”. They will either display a phone number to call or a button to click and will often utilize a little bit of web programming trickery to prevent you from closing the page or navigating away from it.
Like the phone scam discussed above, there is also a single rule to remember in the case of a Browser Hijack:
“Do Not Call The Number”
Don’t call the number or click on any buttons that are displayed on the page. Doing so is essentially the same as calling a telemarketer. Who wants to do that? No, you want to get your computer back so that you can continue what you were doing.
Which brings us to the challenging part: There are multiple ways to fix the issue. Some are quite simple and others more complex. What method will work depends on the type of Hijack. The options below should give you a pretty good idea of how to clear things up though.
-
1. Close the Tab
- This one might sound really obvious but it can be surprisingly effective in some cases. Simply click the little X next to the tab with the offending page and you may find it just closes out nicely. Depending on the type of page, you may have to finagle around with a couple of pop-up JavaScript boxes. You can do this by closing the pop-up box and then quickly pressing the Ctrl + W keys on your keyboard simultaneously to close the tab.
-
2. Restart Your Computer
- An even simpler and more straightforward solution is to simply restart your computer. Several types of Browser Hijacks are nothing more than code insertion into an advertisement or search engine result. For these types of attacks, the easiest resolution is to shutdown and restart. If you can’t access the start menu for some reason, pressing the power button on your computer will normally initiate a shutdown. Pressing and holding the power button will cause your system to turn off immediately. Keep in mind that this will cause you to loose any unsaved work you were doing so be extra careful when attempting to force your computer to turn off.
-
3. Kill the Tab/Browser Process
- If you’re more technically advanced and don’t want to restart your system, you can try simply killing the tab or browser process. To do this just open up the task manager, select the browser process you were using when the hijack occurred, and click “End Task”. This should close down the offending process without needing a full system restart.
-
4. Look for Bad Toolbars or Browser Add-Ons
- Sometimes, repeated Browser Hijackings are caused by add-on toolbars or extensions. These pieces of software are often installed along side other free/paid software. You’ll want to go into the Programs & Features section of the Control Panel (or for Mac users the Applications folder) and look for any software that looks suspicious or appears to be related to the pop-up you’ve been seeing. Uninstalling these applications will allow you to stop the Hijack from recurring. Keep in mind that there is also a lot of legitimate software that will be listed as well, if you are unsure of what you should be uninstalling it might be better to let someone who does know handle it.
If none of the above options work, it’s probably time to ask for help. Consult with either your local technician or feel free to give us a call.
Held for Ransom
Finally, one of the worst types of Hijackers isn’t really a Hijacker. Instead it’s called Ransomware and is far more serious than a simple scam attempt. Unlike a Hijacker, Ransomware actually can lock you out of your computer and potentially cause data loss. If you believe you may be infected with Ransomware, it is important to call us or your local technician right away.
Curious about our products and rates? Visit the About Us page to get a quick run-down of what we offer as well as pricing on our most common services.